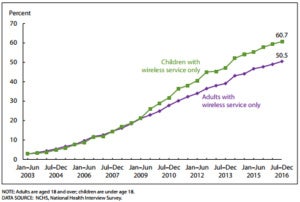
Keeping personal information safe from online hackers has always been a concern. Now that ISPs in the United States have the legal right to sell your internet history without permission, privacy on the web has become a serious issue. Installing an ad blocker or using a browser’s incognito mode doesn’t prevent personal details from leaving your home. If you want to prevent ISP tracking and keep your information secure, the best way to do it is by using a virtual private network.
What Does a VPN Do?
Virtual private networks (VPNs) act as a barrier between your computer and your service provider. Every time you connect to the internet you’re assigned an IP address. This string of numbers is associated with everything you do online, from browsing websites to shopping, watching videos, or checking e-mail, and it can be used to find your location as well as track down your identity. IP activity is logged by service providers and can be accessed by agencies and private parties willing to purchase the information. With a VPN in place, however, that information suddenly becomes useless.

Protect your privacy with a VPN
Simply put, a VPN disguises your internet traffic by scrambling it and passing it through servers around the world. The IP address you’re assigned has no association with yourself or your location, and all traffic is heavily encrypted as it leaves the computer. Instead of seeing personal details and a browsing history, ISPs only receive strings of randomized numbers and letters. Your activity and your information stays private, this is one reason why VPNs are popular for torrenting where users want to hide their activity from their ISP.
How to Choose a VPN
Researching VPNs can get extremely technical. Fortunately you don’t need to know the finer points of IPSec/L2TP and SOCKS5 protocol to make an informed decision. VPNs take care of most of the details, allowing you to focus on picking the provider that best suits your needs.
Which VPN service you go with is ultimately up to you, but there are three basic factors you should research before signing up:
Logging Practices – Logging is a major concern for anyone who’s serious about protecting their privacy online. A VPN provider can know as much about you as an ISP, as they receive all information that passes through your computer. What’s to prevent them from using or selling the data themselves?
Having a strict zero-log or no-log policy is absolutely essential in the VPN you choose. It ensures the company that handles your encrypted data doesn’t store information on their servers. If nothing is stored, nothing can be shared or sold, it’s that simple.
Jurisdiction – Location is extremely important when it comes to a VPN. The physical servers can be positioned almost anywhere, but where the company is registered carries a lot of weight, as the VPN must adhere to local laws. If a country has a strict data retention policy, for example, the VPN will need to comply with any logging and distribution policies, nullifying the effectiveness of the service.
Most high quality VPNs pay close attention to the consumer protection laws they operate under and explicitly state this in their policies. There’s no quick answer to which countries are more privacy friendly with their consumer laws, but VPN users tend to favor providers registered in Iceland, Estonia, Canada, Germany, the US, and Australia.
Cost – If there’s only one rule to remember about choosing a VPN, it’s this: free is almost always a bad idea. Providers that don’t charge customers have almost no incentive to protect your privacy. While it may be tempting to use plug-ins or services that rely on free VPNs, if you’re serious about stopping ISPs from tracking your activity, you’ll need to invest in a paid service. Fortunately most VPNs are available for affordable, flat monthly rates.

VPN Service Recommendations
It’s easy to get lured in by a shady VPN provider. Promises of free service and deep discounts are attractive, especially for first time users. To prevent tracking and keep your information safe, it’s best to stick with a known company that’s been in business for a few years. The examples below are established VPN providers with competitive pricing and are a solid choice for anyone looking to use a VPN.
NordVPN – A long-trusted VPN provider that has 741 servers in 58 countries. The company allows P2P traffic, doesn’t throttle bandwidth, and doesn’t keep logs of any type.
Private Internet Access – Another provider with a good history of reliable service. PIA has a strict zero-log policy, doesn’t monitor or restrict torrent traffic, and has servers available in the US, Iceland, and more.
ExpressVPN – An extremely privacy-oriented VPN provider with offshore jurisdiction based in an independent nation in the Caribbean. A strict zero-log policy and unmonitored traffic makes them a solid choice. For those looking to use a VPN to access geo-restricted content, such as unblocking US Netflix outside of America, ExpressVPN is one of the few that still works.
SlickVPN – A security focused service provider with masked, unmonitored traffic, multiple servers available around the world, and a sturdy zero-log policy.
IPVanish – A popular VPN provider with a focus on speed and anonymity. IPVanish boasts a zero-log policy, no bandwidth monitoring, and over 750 servers spread across 60 countries.
How to Set Up a VPN
Competition has made the process of setting up a VPN extraordinarily simple. The software you download from your chosen network provider will take care of most of the configuration. All you have to do is log in and start using the internet like you always do, only now your personal information is encrypted and safe.
- Sign up with your chosen VPN provider.
- Download the VPN software for each device you use on the internet.
- Install and open the software or app.
- Log in using your VPN credentials.
- Browse the internet and watch videos as normal.
For certain tasks like gaming or heavy video streaming you might want to temporarily disable your VPN to ensure a consistent speed. Always remember to re-enable it afterwards.
Does a VPN Protect Cell Phones and Other Devices?
 A VPN can encrypt data traveling from any internet connected device, but only if you use the service’s software. Signing up with a VPN and installing software on your computer doesn’t automatically protect everything connected to your home network. Unless your VPN provider offers software to add to your router, devices that connect via Wi-Fi will still send unencrypted traffic to your ISP.
A VPN can encrypt data traveling from any internet connected device, but only if you use the service’s software. Signing up with a VPN and installing software on your computer doesn’t automatically protect everything connected to your home network. Unless your VPN provider offers software to add to your router, devices that connect via Wi-Fi will still send unencrypted traffic to your ISP.
To keep your data safe, make sure you download and install apps for every internet device you use, including cell phones, laptops, tablets, and e-readers. Most VPN providers offer easy to use software for iOS and Android devices available from their official website. As an extra bonus, your portable devices will encrypt traffic even when you’re using a public network, adding an extra layer of privacy when you travel.
A VPN You Control
If the thought of sending data to a third party still doesn’t sit right, you can always create and host your own VPN. Sidestepping external providers has a number of advantages, most notably the complete security of encrypting all internet traffic before it leaves your home. You won’t have to worry about VPN privacy policies or zero-log promises being broken. You will, however, need some technical know how and a bit of elbow grease to get it done.
Some of the most popular methods for setting up personal VPNs include OpenVPN and AutoVPN along with a Linux server rented from Amazon or DigitalOcean. The cost is comparable to a third party VPN provider, but with added security and customizability.
 Tuesday, June 6, 2017 at 7:07PM
Tuesday, June 6, 2017 at 7:07PM