A new sophisticated Ransomware attack
 Monday, April 1, 2013 at 2:41PM
Monday, April 1, 2013 at 2:41PM
The authors of police-themed ransomware have started using the browsing histories from infected computers in order to make their scams more believable, according to an independent malware researcher. Ransomware is a class of malicious applications designed to extort money from users by disabling important system functionality or by encrypting their personal files. A particular variation of this type of threat displays messages masquerading as notifications from law enforcement agencies. The language of the messages and the agency names used in them change depending on the location of the victims, but in almost all cases the victims are told that their computers have been locked because they accessed or downloaded illegal content. In order to regain access to their computers, users are asked to pay a fine. A new ransomware variant that employs this trick was spotted over the weekend by an independent malware analyst known online as Kafeine. Dubbed Kovter, this version stands out because it uses information gathered from the victim's browser history in order to make the scam message more credible, Kafeine said Friday in a blog post. Kovter displays a fake warning allegedly from the U.S. Department of Justice, the U.S. Department of Homeland Security, and the FBI, that claims the victim's computer was used to download and distribute illegal content. The message also lists the computer's IP address, its host name, and a website from which the illegal material was allegedly downloaded. The malware checks whether any of the sites already present in the computer's browser history is present in a remote list of porn sites whose content is not necessarily illegal, and if there's a match, it displays it in the message. By using this technique and naming a site that the victim has actually visited as the source for the alleged illegal content, the ransomware authors attempt to increase the credibility of their message. If no match is found when checking the browser history against the remote list, the malware will just use a random porn site in the message, Kafeine said. So beware of this new variant. Just because it may name an actual site you have visited, does not mean it is real.
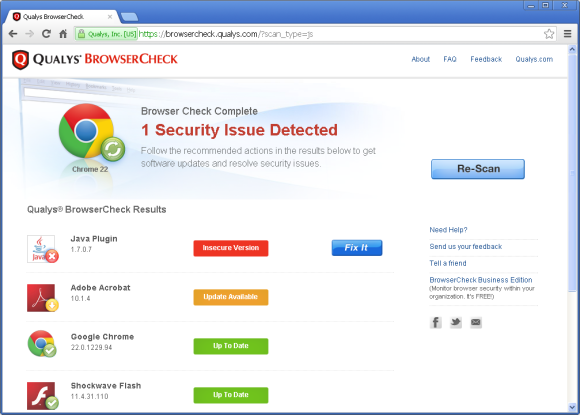 Sample results from a quick Qualys scan. Look at that: The Java plugin needs an update.
Sample results from a quick Qualys scan. Look at that: The Java plugin needs an update.